Cyber Security Consultant Essex: Shield Your Company from Threats
Cyber Security Consultant Essex: Shield Your Company from Threats
Blog Article
Empower Your Organization WITh Trustworthy IT Assistance Providers and Cyber Safety Solutions
In today's quickly evolving electronic landscape, the structure of an effective organization exists in the smooth combination of reputable IT sustain solutions and durable cybersecurity services. With the exponential development of online risks and the increasing complexity of technical systems, businesses deal with a pushing need to fortify their framework versus potential susceptabilities. By leaving your IT requires to experienced professionals and carrying out positive cybersecurity measures, you can protect your operations, safeguard sensitive information, and preserve an one-upmanship out there. The trick to unlocking the complete potential of your business depends on the calculated placement of technology with your business objectives, guaranteeing a secure and durable structure for sustained development.
Importance of Dependable IT Support
In today's digitally-driven business landscape, the significance of dependable IT sustain can not be overemphasized. Services rely heavily on technology to operate effectively and efficiently. From keeping networks to repairing technical issues, having reliable IT sustain guarantees that operations run efficiently without considerable disruptions.
One of the key reasons why dependable IT sustain is important is its duty in decreasing downtime. Any kind of technological problem or system failing can stop service procedures, resulting in lost productivity and income. With efficient and prompt IT support, these issues can be resolved quickly, decreasing downtime and its connected costs.
Moreover, trustworthy IT support plays a crucial role in boosting cybersecurity. In an age where cyber dangers are widespread, having a team of IT specialists makes certain that systems are adequately secured from prospective breaches. These experts carry out durable security steps, screen systems for any kind of suspicious activities, and give prompt updates to protect versus developing cyber threats.

Advantages of Cybersecurity Solutions
Provided the vital duty of trusted IT sustain in reducing downtime and enhancing cybersecurity, it is important to highlight the considerable benefits that cybersecurity solutions give services in today's digital landscape. Cybersecurity remedies play an essential function in securing delicate data and safeguarding businesses from cyber dangers. One of the vital benefits is the prevention of information breaches, which can result in extreme monetary and reputational damages. By carrying out robust cybersecurity actions, companies can maintain the count on of their partners and consumers.
Cybersecurity services make it possible for businesses to identify and respond to cyber occurrences quickly, decreasing the influence of possible protection violations. Inevitably, spending in cybersecurity solutions not just safeguards businesses from cyber risks yet additionally adds to their long-lasting sustainability and growth in a significantly digital globe.
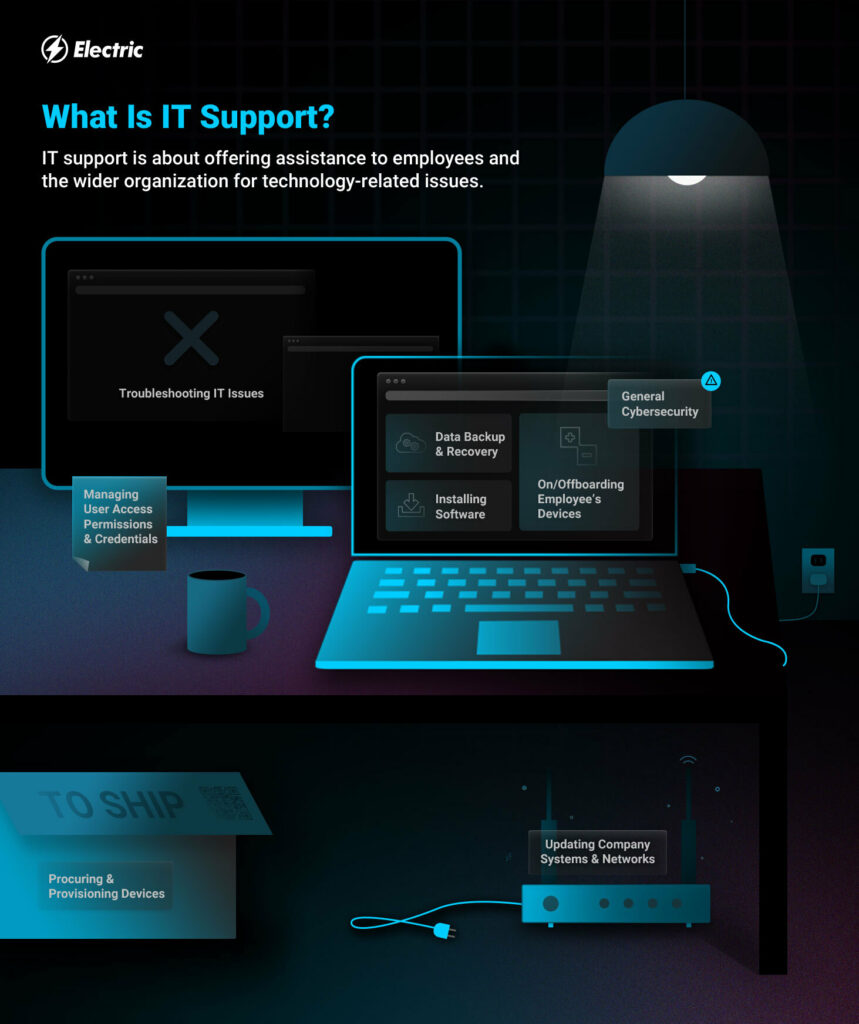
Choosing the Right IT Provider
To effectively meet the technological needs of your company, selecting the ideal IT services is paramount. When selecting IT solutions, it is vital to think about several essential variables to guarantee that the solutions straighten with your company purposes. Begin by assessing your details demands and purposes to determine the kind of IT solutions that will best support your procedures. Consider the scalability of the IT solutions to accommodate your organization's development and developing needs. Search for a solution company with a tested performance history of dependability and know-how in the solutions you call for. It is additionally vital to evaluate the level of consumer assistance given by the IT solution company to guarantee that you will get prompt assistance whenever needed. Furthermore, take into consideration the cybersecurity measures and methods carried out by the solution supplier to safeguard your business information and systems. By very carefully reviewing these aspects, you can pick the appropriate IT services that will equip your service and drive success.
Executing Cybersecurity Actions
Applying robust cybersecurity measures is an essential facet of securing your business's sensitive data and making certain the stability of your systems. Cyber hazards continue to advance in refinement and regularity, making this link it imperative for organizations to proactively shield themselves. To improve cybersecurity, start by conducting a comprehensive danger evaluation to identify vulnerabilities and prospective entry factors for harmful actors. Implementing multi-factor verification, security methods, and normal security updates can aid fortify your defenses.
Routine security audits and infiltration screening can better examine the efficiency of your cybersecurity actions and determine locations for enhancement. By focusing on cybersecurity and remaining aggressive in your strategy, you can much better protect your organization from cyber hazards and possible information violations.
Ensuring Service Continuity
After applying robust cybersecurity actions to protect your company's sensitive data, the emphasis changes towards ensuring organization connection despite prospective disturbances. Business continuity preparation is important for mitigating threats and keeping operations throughout unexpected occasions such as natural calamities, cyber-attacks, or system failings. One key aspect of making certain business continuity is the development of a comprehensive connection plan that lays out strategies for maintaining necessary functions and solutions. This strategy must incorporate treatments for data backup and recovery, different interaction methods, and worker duties and duties during a situation.
Additionally, regular screening and upgrading of the continuity plan are important to guarantee its performance when needed. Services ought to perform drills and simulations to identify weaknesses in the plan and make required improvements. Additionally, having redundant systems and backup remedies in position can help lessen downtime and make sure seamless operations in case of interruptions. By focusing on service connection, companies can boost their strength and reduce the impact of potential risks on their procedures and track record.
Conclusion
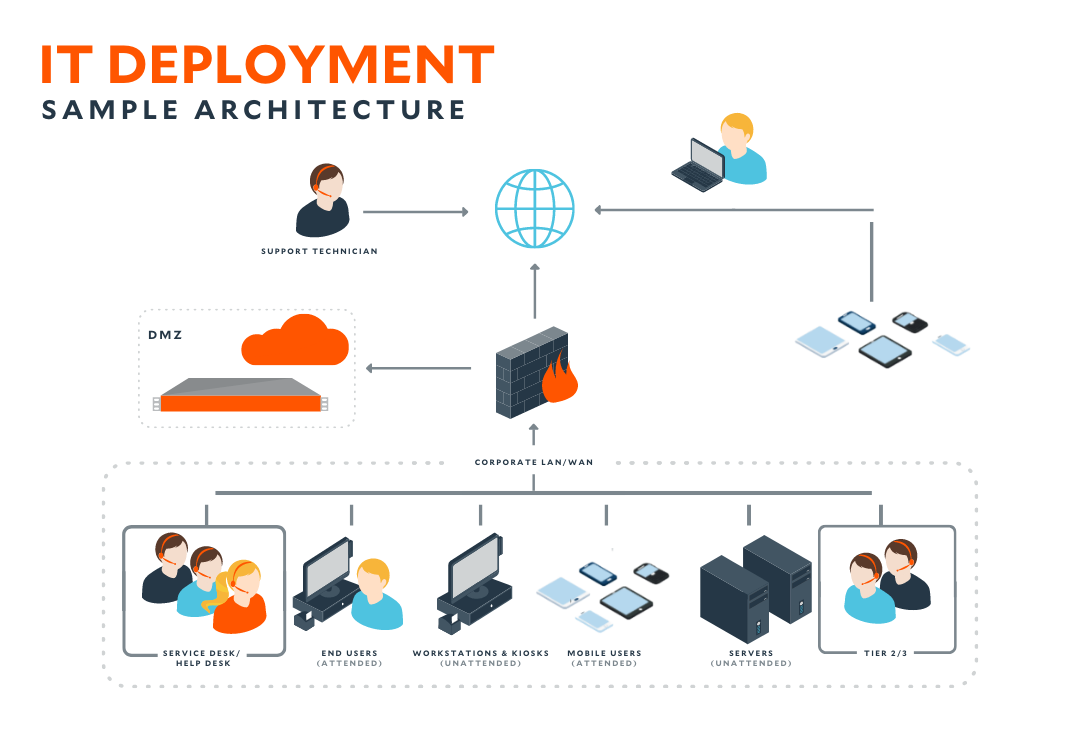
In today's quickly advancing electronic page landscape, the structure of an effective anonymous business exists in the smooth combination of reliable IT support solutions and robust cybersecurity solutions.Offered the critical function of reputable IT sustain in reducing downtime and boosting cybersecurity, it is important to highlight the substantial benefits that cybersecurity solutions bring to businesses in today's digital landscape.After applying robust cybersecurity actions to secure your service's sensitive information, the focus shifts towards guaranteeing business connection in the face of prospective disturbances.In final thought, trustworthy IT sustain services and cybersecurity remedies are essential for encouraging organizations to operate successfully and firmly. It is vital for services to focus on spending in IT support and cybersecurity to guard their operations and preserve an affordable edge in today's electronic landscape.
Report this page